Authors: Stephen Cook (RHUL), Maryam Mehrnezhad (RHUL), Ehsan Toreini (University of Surrey)
We are pleased to announce that we have published a new paper in the Springer International Journal of Information Security. Link to open-access full paper: https://link.springer.com/article/10.1007/s10207-024-00883-3
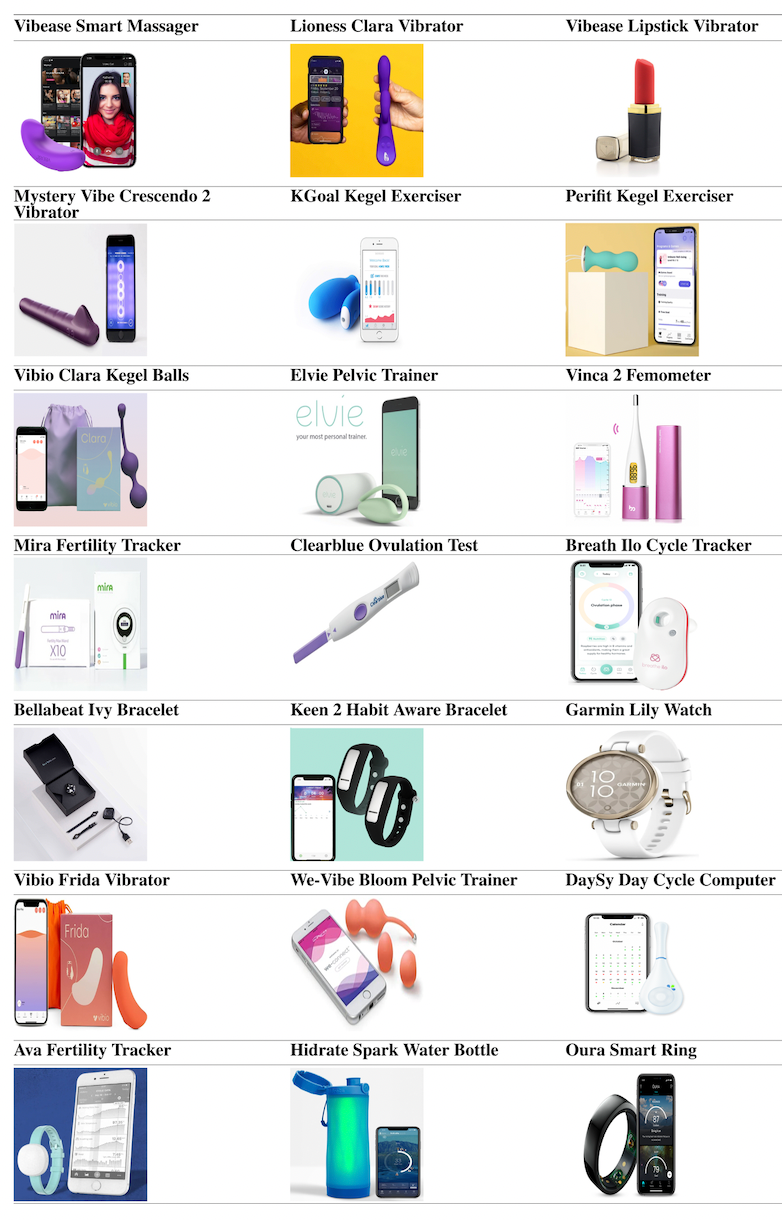
The adoption of commercial digital health technologies is increasing faster than ever with its global market share predicted to reach a value of $657 Billion by 2025. These products encompass mobile apps and connected Internet of Things (IoT) devices. They collect various data regarding their users including health, medical, psychological, sex life, and other intimate data. These new digital health technologies introduce new risks to users from malicious attackers. In our research we investigated the security of Bluetooth Low Energy (BLE) a popular wireless communication technology used for facilitating communication, of 21 Female-orientated (FemTech) IoT devices see Figure 1. Following our initial findings, we then targeted a subset of 3 FemTech devices and instigated a series of Bluetooth attacks against with most of them being successful. Finally, we also studied the use of permissions and trackers in the devices companion mobile apps.
What is FemTech?
FemTech is the term applied to a range of digital health, products, tools, software, diagnostics, systems and services that use technology often to focus on women’s health. They can focus on specific areas of health care such as reproductive health (e.g., menstruation, fertility, menopause) and/or general, mental and physical wellbeing. Previous research has examined the various threat actors that are interested in FemTech data. Some examples include family members, ex-(partners), and cyber criminals. As well as the Types of data that are collected by these IoT devices. Due to the types of FemTech data and systems, there is no single law to ensure the protection of the data as it can be related to regulations regarding UK GDPR, Medical, health, and human rights to name a few.
What did we do?
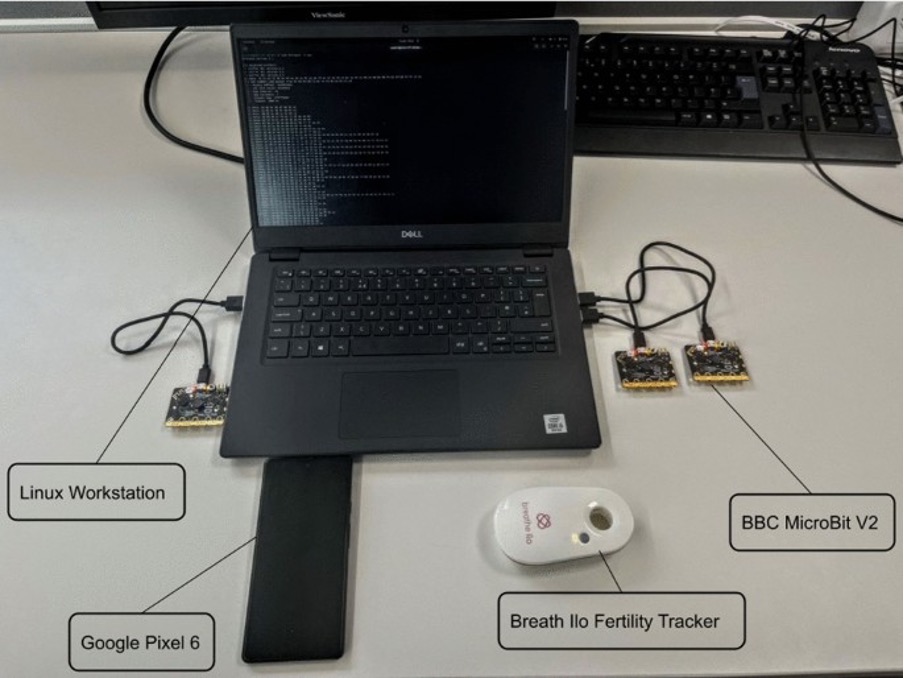
In our research, we studied a set of 21 Internet of Things (IoT) devices which were advertised for general and/or intimate health purposes of female bodies (aka female-oriented technologies or FemTech). This is, to the best of our knowledge, the largest study of its kind so far. We focused on the security of the Bluetooth communications between the IoT device and their apps. We assessed the Bluetooth communications using off the shelf BBC Microbits V2 and publicly available software that requires limited technical knowledge to use. We targeted a subset of 3 devices and instigated a series of targeted attacks against them highlighting the potential impact an attacker may have on both device and user. The device apps were also analysed using Exodus Privacy analysis which allows to view the system permissions used by the app and identify if online trackers were present. Finally, we reported our findings to the device vendors before publicly disclosing them.
Are these FemTech IoT devices secure?
The results of our research highlighted that 20 out of 21 of the devices tested used “Just Works” pairing mode in their Bluetooth communications. This pairing mode requires no authentication, as a result, any phone/device can connect to the FemTech device without necessarily being the genuine user. Further 17 devices did not employ encryption during transmission of the device traffic. Finally, some of the devices tested Bluetooth Low Energy 4.0 a version of Bluetooth that was first released in 2010, despite the earliest release date of our devices being 2019.
We also investigated the Bluetooth services running on these devices and found that all of them used 1 or more custom Bluetooth service designed by the device vendors. This is a significant challenge for security auditing as these services are not created by the Bluetooth Special Interest Group which designs and documents the Bluetooth specification. Meaning that we have no documentation to refer to when analysing device BLE traffic increasing the difficulty in determining what data is being sent. The majority of our targeted Bluetooth attacks against our subset FemTech Devices were also successful, For the full results please see the open-access full paper: https://link.springer.com/article/10.1007/s10207-024-00883-3
| Devices Attack type | Hidrate Spark 3 water bottle | Breath Ilo fertility tracker | We-Vibe Bloom pelvic trainer |
| MITM Replay | Successful Successful | Unsuccessful Unsuccessful | Successful Successful |
| Connection Hijack Denial of Service Denial of Sleep | Successful Successful Successful | Successful Successful Unsuccessful | Successful Successful Successful |
Recommendations
We recommend that device developers implement the most recent security & privacy considerations outlined by the Bluetooth SIG. Companies should ensure that encryption is applied in sending and receiving data via Bluetooth. One of our main findings was that the majority of devices used JW pairing which does not provide user authentication when exchanging encryption keys. Developers should implement alternative BLE pairing methods. One such pairing method is Out Of Band (OOB) which uses other system resources such as cameras or Near Field Communication (NFC) to authenticate and exchange encryption keys.
The apps themselves often included excessive permissions for the task they were designed for, they also contained online trackers. The app permissions should be regularly reviewed, and non-necessary or outdated permissions removed. The presence of online trackers should be clearly and regularly communicated to the user.